コムスコープの世界をリードするネットワークソリューションのポートフォリオの一部である RUCKUS Networks へようこそ。詳細
In the network and security world, there is a famous story about a casino that was hacked, and the story behind that hack is worthy of an uncomfortable chuckle. It was discovered after some digging that the point of access for the crime’s perpetrators was an IoT device. Specifically, the heater in a fish tank that had just been installed was the weak point in their network security that allowed the hackers access to the casino’s network and eventual exfiltration of the casino’s information – information like high rollers, clients, and other operational data, all copied through the fish tank heater.
The facetious moral of the story here, is “when your fish tank is sending Gigabytes of data to other countries, that’s a problem.” The actual lesson is that you should be able to flag any device that is not following its “normal” activity.
In the past, this problem was usually solved by someone in the organization making a policy stating that all devices that will connect to the network will be required to pass a rigorous screening process. If you have ever been a part of that, you also know that this works until someone with the right letters after their name overrides that policy for “their” devices and then it quickly falls apart.
The solution for instances like this, and it’s not going away, is to build and plan for these IoT devices from the network side of the house. The US Federal Government recently announced a new program to help secure IoT devices, but it’s going to take time to get everyone up to speed, and the certification is voluntary, so it will require businesses to design networks based upon acquiring certified secure devices. Not allowing these devices on the network, as most network engineers know, is also not an option.
While the task might be daunting, RUCKUS Networks has some avenues to help network architects and administrators handle these devices that weren’t really designed to be utilized in an enterprise situation.
Wi-Fi IoT Devices
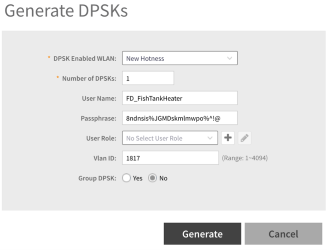 Wi-Fi IoT devices are the easiest and simplest IoT devices to deal with when using a RUCKUS network. Every RUCKUS controller platform has a solution included called Dynamic Pre-Shared Key, or DPSK – a RUCKUS innovation over a decade ago that is still going strong. DPSK allows for device management much like you see with Dot1X solutions but using WPA2-Personal. Each device is assigned its own passphrase for a single SSID, and it uses that passphrase to join the network. As part of this configuration, each device can be assigned to a specific VLAN.
Wi-Fi IoT devices are the easiest and simplest IoT devices to deal with when using a RUCKUS network. Every RUCKUS controller platform has a solution included called Dynamic Pre-Shared Key, or DPSK – a RUCKUS innovation over a decade ago that is still going strong. DPSK allows for device management much like you see with Dot1X solutions but using WPA2-Personal. Each device is assigned its own passphrase for a single SSID, and it uses that passphrase to join the network. As part of this configuration, each device can be assigned to a specific VLAN.
Let’s be honest, no one ever wants a fish tank heater on a VLAN that has access to corporate databases. That sounds bad just typing it outI Also, my apologies if the passphrase 8ndnsis%JGMDskmlmwpo%^!@ is yours, you might want to change it now. Once the IoT device is placed on a specific VLAN, either by itself or part of a larger IoT VLAN, network configurations can now be used to isolate that VLAN using different tunneling configurations as well as using firewalls to manage what those devices are allowed to talk to, in addition to monitoring the network traffic of those device to make sure they aren’t talking to random countries they have no business communicating with.
We might not be able to modify how the device is programmed but we can use existing methodologies to contain and monitor the device.
The other thing about DPSK is, if some nefarious person hanging out around the fish tank decides to steal the heater to gain access to your network, you can simply delete the DPSK from the network controller and the device loses all access to the network and that passphrase is now useless.
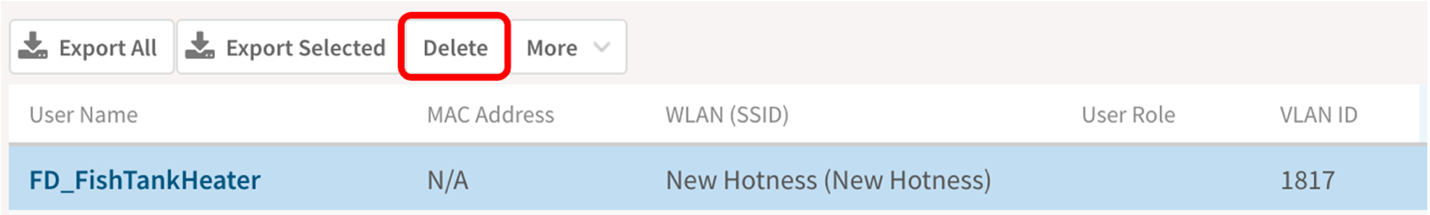
If you are using Cloudpath, you can simply revoke the DPSK using the built-in management functionality.
DPSK works on any device that can support WPA2-Personal making it universally supported in Wi-Fi. Lastly, it took IoT devices almost a decade to add 5 GHz radios to their devices so WPA3 support isn’t even on their roadmap yet.
“Other” IoT Devices
DPSK is great as almost all Wi-Fi devices support it, but non-Wi-Fi devices like ZigBee, BLE, and other 802.15.4 devices do not; this is where the fear of IoT devices comes from. Unlike Wi-Fi devices which, once they are on the network like all our other devices, can be tracked and managed, most IoT devices operate outside the 802.11 standard so they can’t be managed and tracked the same way. This is where the RUCKUS IoT Suite, more specifically the RUCKUS IoT Controller (RIoT) comes into play.
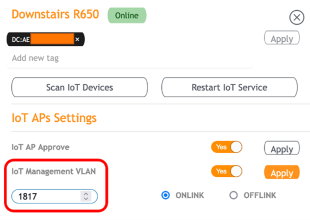 RUCKUS Wi-Fi 5, 6, & 6E APs are all ready to handle your IoT network needs. The Wi-Fi 5 APs are going to need a USB radio plugged into the USB port of the AP while the Wi-Fi 6 & 6E APs (the exception being the R350) all have IoT radios included. This built-in capability means that many people already have IoT support in their network, even if they don’t realize it.
RUCKUS Wi-Fi 5, 6, & 6E APs are all ready to handle your IoT network needs. The Wi-Fi 5 APs are going to need a USB radio plugged into the USB port of the AP while the Wi-Fi 6 & 6E APs (the exception being the R350) all have IoT radios included. This built-in capability means that many people already have IoT support in their network, even if they don’t realize it.
The RIoT controller is to IoT devices what the WLAN controllers are to Wi-Fi – a place to manage and control the IoT devices that appear on your network. Once your IoT APs are synchronized to RIoT, network administrators now have control and visibility of their IoT devices that most have never seen before. IoT radios can be controlled in the same way that WLAN administrators are used to managing their Wi-Fi radios. IoT devices have a multi-step process to join the network and can be placed into their own IoT VLAN, again just like with Wi-Fi devices.
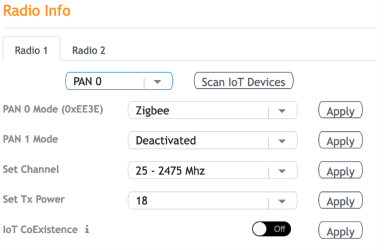 When ready, each radio can be put into scan mode and, as devices are discovered, they can either be approved to join the network or blacklisted, whichever is appropriate for that device.
When ready, each radio can be put into scan mode and, as devices are discovered, they can either be approved to join the network or blacklisted, whichever is appropriate for that device.
If this manual process seems overwhelming, there is the ability to upload a CSV file containing your intended IoT devices to put them into a pre-approved list. Once discovered, they are automatically added to the controller. During this process, tags and the intended IoT AP can also be defined.
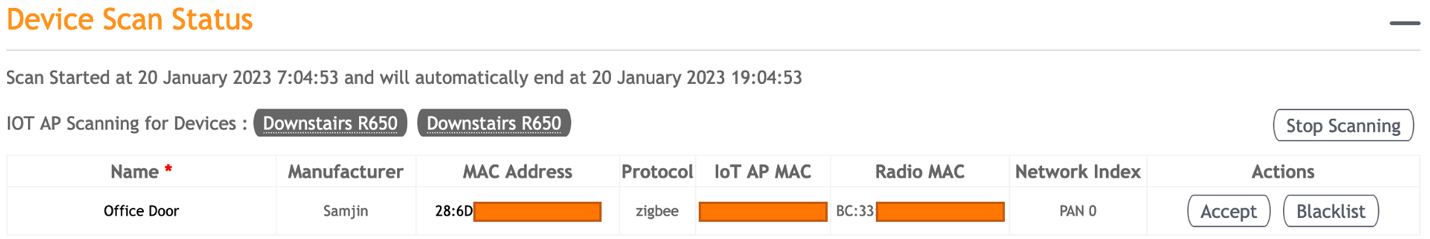
The thing to keep in mind is security and ease of onboarding never truly align. When security is a priority, then on-boarding and management will always have a certain time cost associated with it. Our goal here isn’t to remove any work from the network administrators’ plate, just to help them manage it.
As with the Wi-Fi IoT devices and DPSK, if a device goes offline, that device will show up in the RIoT dashboard as offline and can then be investigated and removed/blacklisted from the network if required.
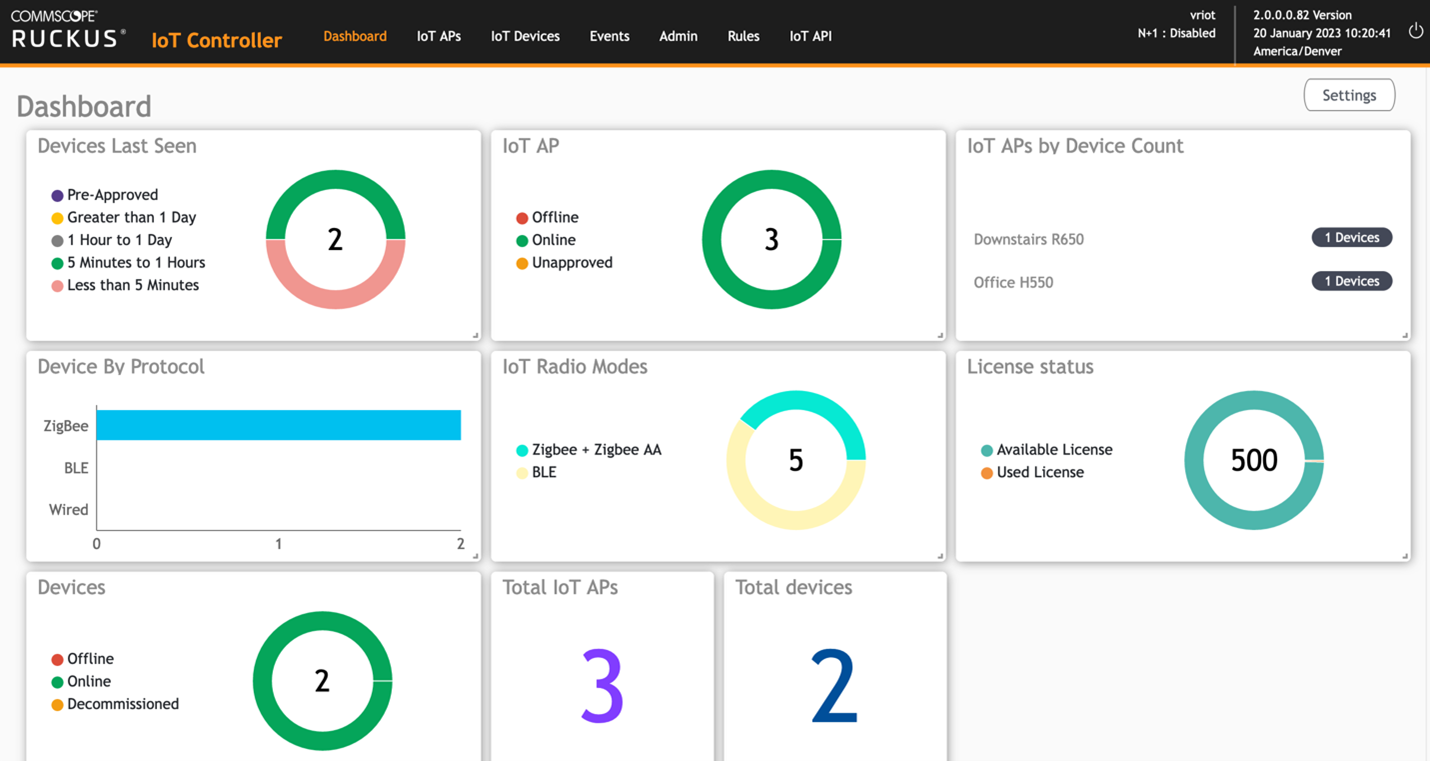
RUCKUS IoT Controller Dashboard
Any security professional will tell you that the first step to securing your network is understanding what is connected to your network and then having control over those devices. The RUCKUS IoT Controller offers the control and visibility that security professionals want, and network professionals need. From controlling the device, to removing it from the network, to managing VLANs and code upgrade, RIoT can be the operational platform that ticks all the check boxes of the security team.
While RUCKUS Networks cannot control the market when it comes to security built into IoT devices or the manufacturers of these devices, we can at least help network operators manage, control, and secure these devices once they are introduced into their operating environment.
The following resources can help you learn more about the RUCKUS Networks solutions:
- APs with integrated IoT radios
- IoT Ready APs that can use a external IoT radio plugged into the USB port
- RUCKUS Controller platforms like SmartZone or RUCKUS One.
- RUCKUS IoT Controller
To learn more about the RUCKUS Networks IoT Solution, you can visit the product page or contact us to have someone help your organization realize the full potential of what IoT can do for you.













